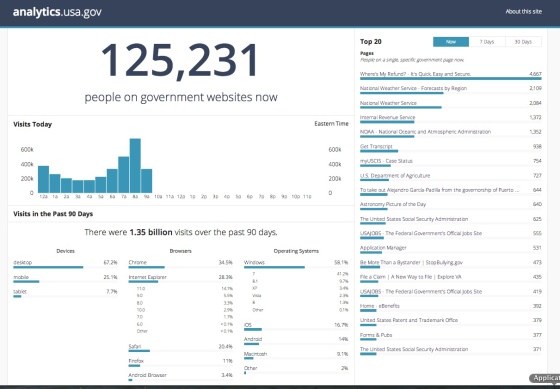
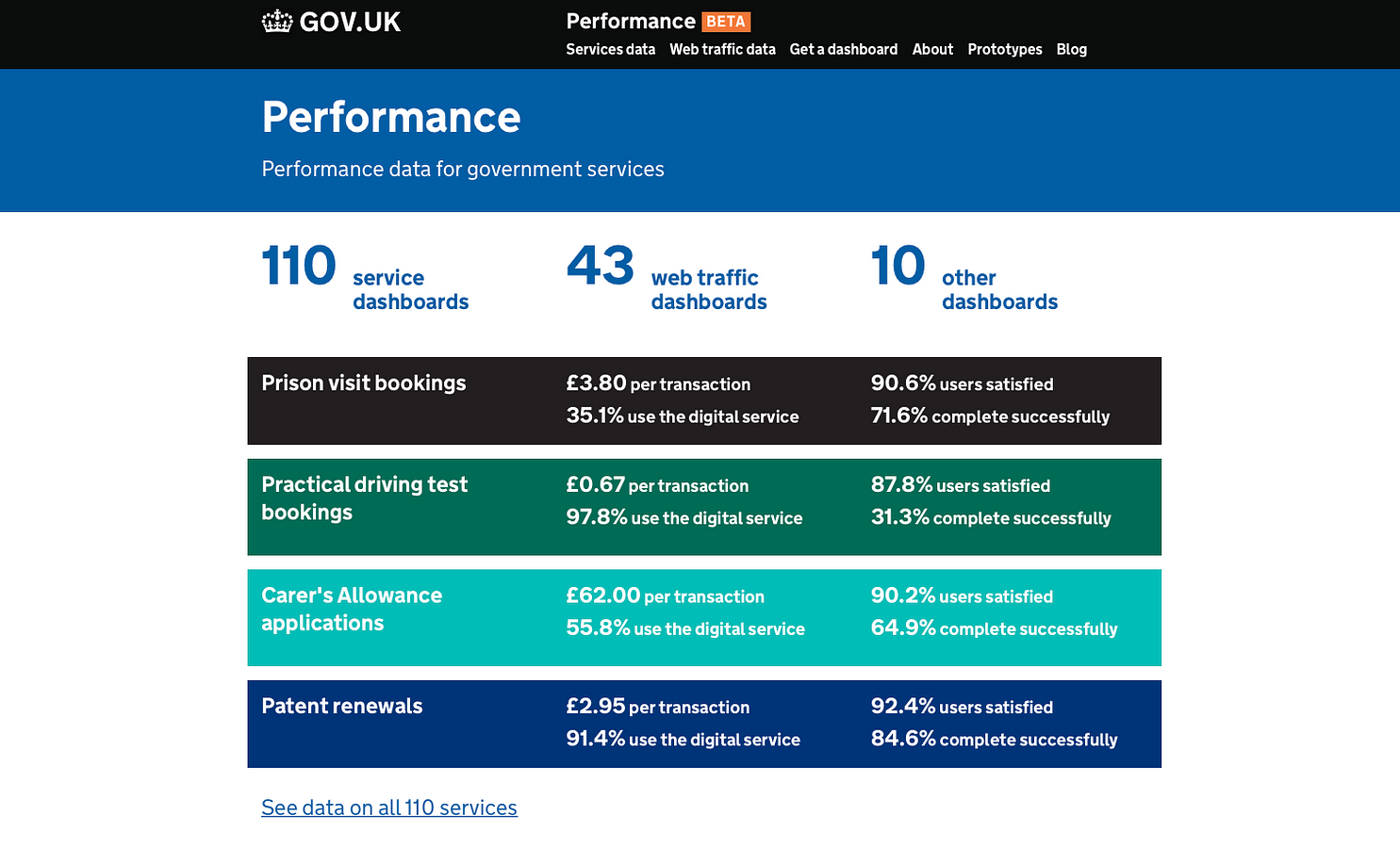
In its search for technology talent, the White House has been recruiting heavily from Google of late, including U.S. chief technology officer Megan Smith. Today, President Barack Obama showed that his administration also likes Facebook, announcing that engineer David Recordon would upgrade the White House’s technology infrastructure. The news was first reported by Yahoo.
“In our continued efforts to serve our citizens better, we’re bringing in top tech leaders to support our teams across the federal government,” said President Obama, in a statement. “Today, I’m pleased to welcome David Recordon as the Director of White House Information Technology. His considerable private sector experience and ability to deploy the latest collaborative and communication technologies will be a great asset to our work on behalf of the American people.”
On the one hand, it’s terrific to see The White House attract top tech talent. Getting David Recordon into public service should be a win for the American people. Based upon a somewhat cryptic hint he posted on Facebook last August, it appeared that he was involved in helping to fix Heathcare.gov and another unnamed important project. The blog post that went up at WhiteHouse.gov confirmed that Recordon was “one of those engineers.” Bringing the best engineers the administration can find into the U.S. Digital Service will help the nation avoid more IT catastrophes, and Recordon, a notable open standard advocate who helped develop OpenID, is clearly one of them. That’s good news.
On the other hand, while being the first “Director of White House Information Technology” is clearly great copy for the tech press, working to “ensure that the technology utilized by the White House is efficient, effective, and secure” sounds more or less what the White House chief information officer should be — and has been – doing for years.
Just look at the responsibilities for the Office of the CIO. Per Federal News Radio, the White House CIO for the past two years, Karen Britton, stepped down in January 2015, without any announced replacement since. Michael Hornsby, the director of engineering and operations within OCIO, served as acting CIO. This all leads me to hypothesize that Recordon has effectively been named the new White House CIO but doesn’t have that title.
Regardless, here’s hoping Recordon’s considerable expertise leads to improvements in an information technology infrastructure that has come a long way since 2009 (read this) but still lags the private sector.
President Obama signed an official presidential memorandum today creating the role and establishing an “Executive Committee for Presidential Information Technology” made up of the “Assistant to the president for Management and Administration, the Executive Secretary of the National Security Council, the Director of the Office of Administration, the Director of the United States Secret Service, and the Director of the White House Military Office.”
According to the memorandum, which is embedded beneath and reproduced in plaintext below (it’s not online at WhiteHouse.gov yet), this committee will “shall advise and make policy recommendations to the Deputy Chief of Staff for Operations and the Director with respect to operational and procurement decisions necessary to achieve secure, seamless, reliable, and integrated information resources and information systems for the President, Vice President, and EOP.”
In other words, these folks will advise the director on how to by, build and run tech for the White House.
Presidential Memorandum White House IT:
https://www.scribd.com/embeds/259313174/content?start_page=1&view_mode=scroll&show_recommendations=true
[Photo Credit: Brian Solis]
THE WHITE HOUSE
Office of the Press Secretary
For Immediate Release March 19, 2015
March 19, 2015
MEMORANDUM FOR THE SECRETARY OF DEFENSE
THE SECRETARY OF HOMELAND SECURITY
THE DIRECTOR OF THE OFFICE OF MANAGEMENT AND
BUDGET
THE NATIONAL SECURITY ADVISOR
THE DIRECTOR OF THE OFFICE OF ADMINISTRATION
SUBJECT: Establishing the Director of White House
Information Technology and the Executive
Committee for Presidential Information Technology
By the authority vested in me as President by the Constitution
and the laws of the United States of America, and in order to
improve the information resources and information systems
provided to the President, Vice President, and Executive Office
of the President (EOP), I hereby direct the following:
Section 1. Policy. The purposes of this memorandum are to
ensure that the information resources and information systems
provided to the President, Vice President, and EOP are
efficient, secure, and resilient; establish a model for
Government information technology management efforts; reduce
operating costs through the elimination of duplication and
overlapping services; and accomplish the goal of converging
disparate information resources and information systems for the
EOP.
This memorandum is intended to maintain the President’s
exclusive control of the information resources and information
systems provided to the President, Vice President, and EOP.
High-quality, efficient, interoperable, and safe information
systems and information resources are required in order for the
President to discharge the duties of his office with the support
of those who advise and assist him, and with the additional
assistance of all EOP components. The responsibilities that
this memorandum vests in the Director of White House Information
Technology, as described below, have been performed historically
within the EOP, and it is the intent of this memorandum to
continue this practice.
The Director of White House Information Technology, on
behalf of the President, shall have the primary authority to
establish and coordinate the necessary policies and procedures
for operating and maintaining the information resources and
information systems provided to the President, Vice President,
and EOP. Nothing in this memorandum may be construed to
delegate the ownership, or any rights associated with ownership, 2
of any information resources or information systems, nor of any
record, to any entity outside of the EOP.
Sec. 2. Director of White House Information Technology.
(a) There is hereby established the Director of White House
Information Technology (Director). The Director shall be the
senior officer responsible for the information resources and
information systems provided to the President, Vice President,
and EOP by the Presidential Information Technology Community
(Community). The Director shall:
(i) be designated by the President;
(ii) have the rank and status of a commissioned
officer in the White House Office; and
(iii) have sufficient seniority, education, training,
and expertise to provide the necessary advice,
coordination, and guidance to the Community.
(b) The Deputy Chief of Staff for Operations shall provide
the Director with necessary direction and supervision.
(c) The Director shall ensure the effective use of
information resources and information systems provided to the
President, Vice President, and EOP in order to improve mission
performance, and shall have the appropriate authority to
promulgate all necessary procedures and rules governing these
resources and systems. The Director shall provide policy
coordination and guidance for, and periodically review, all
activities relating to the information resources and information
systems provided to the President, Vice President, and EOP by
the Community, including expenditures for, and procurement of,
information resources and information systems by the Community.
Such activities shall be subject to the Director’s coordination,
guidance, and review in order to ensure consistency with the
Director’s strategy and to strengthen the quality of the
Community’s decisions through integrated analysis, planning,
budgeting, and evaluation processes.
(d) The Director may advise and confer with appropriate
executive departments and agencies, individuals, and other
entities as necessary to perform the Director’s duties under
this memorandum.
Sec. 3. Executive Committee for Presidential Information
Technology. There is hereby established an Executive Committee
for Presidential Information Technology (Committee). The
Committee consists of the following officials or their
designees: the Assistant to the President for Management and
Administration; the Executive Secretary of the National Security
Council; the Director of the Office of Administration; the
Director of the United States Secret Service; and the Director
of the White House Military Office.
Sec. 4. Administration. (a) The President or the Deputy
Chief of Staff for Operations may assign the Director and the
Committee any additional functions necessary to advance the
mission set forth in this memorandum.
(b) The Committee shall advise and make policy
recommendations to the Deputy Chief of Staff for Operations and
the Director with respect to operational and procurement 3
decisions necessary to achieve secure, seamless, reliable, and
integrated information resources and information systems for the
President, Vice President, and EOP. The Director shall update
the Committee on both strategy and execution, as requested,
including collaboration efforts with the Federal Chief
Information Officer, with other government agencies, and by
participating in the Chief Information Officers Council.
(c) The Secretary of Defense shall designate or appoint a
White House Technology Liaison for the White House
Communications Agency and the Secretary of Homeland Security
shall designate or appoint a White House Technology Liaison for
the United States Secret Service. Any entity that becomes a
part of the Community after the issuance of this memorandum
shall designate or appoint a White House Technology Liaison for
that entity. The designation or appointment of a White House
Technology Liaison is subject to the review of, and shall be
made in consultation with, the President or his designee. The
Chief Information Officer of the Office of Administration and
the Chief Information Officer of the National Security Council,
and their successors in function, are designated as White House
Technology Liaisons for their respective components. In
coordination with the Director, the White House Technology
Liaisons shall ensure that the day-to-day operation of and
long-term strategy for information resources and information
systems provided to the President, Vice President, and EOP are
interoperable and effectively function as a single, modern, and
high-quality enterprise that reduces duplication, inefficiency,
and waste.
(d) The President or his designee shall retain the
authority to specify the application of operating policies and
procedures, including security measures, which are used in the
construction, operation, and maintenance of any information
resources or information system provided to the President, Vice
President, and EOP.
(e) Presidential Information Technology Community entities
shall:
(i) assist and provide information to the Deputy
Chief of Staff for Operations and the Director,
consistent with applicable law, as may be necessary to
implement this memorandum; and
(ii) as soon as practicable after the issuance of
this memorandum, enter into any memoranda of
understanding as necessary to give effect to the
provisions of this memorandum.
(f) As soon as practicable after the issuance of this
memorandum, EOP components shall take all necessary steps,
either individually or collectively, to ensure the proper
creation, storage, and transmission of EOP information on any
information systems and information resources provided to the
President, Vice President, and EOP.
Sec. 5. Definitions. As used in this memorandum:
(a) “Information resources,” “information systems,”
and “information technology” have the meanings assigned by
section 3502 of title 44, United States Code.4
(b) “Presidential Information Technology Community” means
the entities that provide information resources and information
systems to the President, Vice President, and EOP, including:
(i) the National Security Council;
(ii) the Office of Administration;
(iii) the United States Secret Service;
(iv) the White House Military Office; and
(v) the White House Communications Agency.
(c) “Executive Office of the President” means:
(i) each component of the EOP as is or may
hereafter be established;
(ii) any successor in function to an EOP component
that has been abolished and of which the function is
retained in the EOP; and
(iii) the President’s Commission on White House
Fellowships, the President’s Intelligence Advisory
Board, the Residence of the Vice President, and such
other entities as the President from time to time may
determine.
Sec. 6. General Provisions. (a) Nothing in this
memorandum shall be construed to impair or otherwise affect:
(i) the authority granted by law to an executive
department, agency, entity, office, or the head
thereof; or
(ii) the functions of the Director of the Office of
Management and Budget relating to budgetary,
administrative, or legislative proposals.
(b) This memorandum shall be implemented consistent with
applicable law and appropriate protections for privacy and civil
liberties, and subject to the availability of appropriations.
(c) This memorandum is not intended to, and does not,
create any right or benefit, substantive or procedural,
enforceable at law or in equity by any party against the
United States, its departments, agencies, or entities, its
officers, employees, or agents, or any other person.
BARACK OBAMA
# # #